MWA Responsibilities, Menu and Functions
- The way we create responsibilities, menus and functions is similar to other oracle applications.
Responsibilities:
- Responsibilities should have "Oracle Mobile Applications" selected in "Available From".
Menu:
- Menu are normally created with menu type "Standard".
Function:
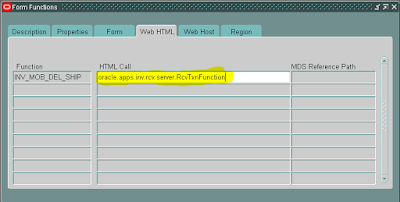
- Function should be created with type "Mobile Applications".
- HTML Call of the function should point to java class full name for menu item bean (We'll discuss more on this in coming section.
Technical Overview of MSCA/MWA Framework
In technical overview of the MSCA/MWA Framework, we need to understand Mobile Application Beans (Mobile Application Screen UI Construction) and Event Listener Model (Event Handling like Page Enter, Field Exit, Button click etc):
Mobile Application Beans
Following are key Mobile Application Beans:
oracle.apps.mwa.beans.MWABeanpublic class MWABean extends java.lang.Object implements java.io.Serializable- Base class for all UI beans.
- MenuItemBean, PageBean, FieldBean, FlexfieldBean all extend from this class.
- Maintains a list of MWA event listeners (
protected java.util.Vector m_listeners). public void addListener(MWAListener Listener)public void removeListener(MWAListener Listener)public java.util.Vector getListeners()- We don't use this bean directly in our coding.
oracle.apps.mwa.beans.MenuItemBeanpublic class MenuItemBean extends MWABean- Connects FND Menu Structure to Mobile Application. FND Form function for the Mobile Application points to a MenuItemBean.
- As per naming convention, MenuItemBean ends with suffix "
Function". - It stores the key name of the first page of the mobile application (
protected java.lang.String m_firstPageName). public java.lang.String getFirstPageName()
public void setFirstPageName(java.lang.String FirstPageName)
- Example - Following statement is typically written in the Constructor:
- setFirstPageName("xxabc.oracle.apps.abc.xyz.inv.invtxn.server.MyFirstCustomPage");
- FirstCustomPage is custom PageBean.
- Other functions it provides are to set/get the menu confirmation message:
public void setMenuConfirmMessage(java.lang.String msg)
public java.lang.String getMenuConfirmMessage()
oracle.apps.mwa.beans.PageBeanpublic class PageBean extends MWABean- Base class for all user developed page level beans.
- Contains the page prompt which is displayed to the end user as the title of the page (
protected java.lang.String m_prompt) public void setPrompt(java.lang.String Prompt)public java.lang.String getPrompt()- Maintains list of field beans which are part of this page (
protected java.util.Vector m_fieldBeans) and current field indicator (protected int m_curtField): public void addFieldBean(FieldBean FB)public void addFieldBean(int index, FieldBean FB)public void removeFieldBean(FieldBean FB)public void removeAllFieldBeans()public int getCurrentFieldIndex()public int getFieldIndex(java.lang.String key)public FieldBean getCurrentFieldBean()public java.util.Vector getFieldBeanList()public void setFieldBeanList(java.util.Vector BeanList)- Contains Session for the page (
protected Session m_session) Session Handling methods: public Session getSession()public void setSession(Session sessionObject)Other key methods:- To return the full name of the pagebean:
public java.lang.String getName() - To mark if a page bean is to be instantiated upon each visit during runtime:
public boolean isMultipleInstance(), public void setMultipleInstance(boolean MultipleInstance) - Typically as first step, we declare the FieldBeans in pageBean class's declaration section, and generate getters and setters for the fieldbeans. In Constructor to add field beans, modify fieldbean properties, change the order of the fieldbeans, associate field Listener to field beans (Details on FieldListener will be covered later).
- For code examples - please refer FieldBean.
oracle.apps.mwa.beans.FieldBeanpublic class FieldBean extends MWABean- Base class for all field level beans.
- Important Subclasses -
ButtonFieldBean, HeadingFieldBean, InputableFieldBean (With Subclasses - LOVFieldBean, MultiListFieldBean, TextFieldBean), ListFieldBean, MessageFieldBean. - Maintains name property of the field (
protected java.lang.String m_name) public java.lang.String getName()public void setName(java.lang.String Name)- Maintains prompt property of the field (
protected java.lang.String m_prompt) public java.lang.String getPrompt()public void setPrompt(java.lang.String Prompt)- Maintains hidden property of the field (
protected boolean m_hidden) public boolean isHidden()public void setHidden(boolean Hidden)- Maintains type of field (
protected short m_type): - default is
INPUTTEXT. public int getType()- Possible Values include:
- public static short TEXT
- public static short LOV
- public static short MULTILIST
- public static short LIST
- public static short BUTTON
- public static short CHECKBOX
- public static short RADIO
- public static short HEADING1
- public static short HEADING2
- public static short LINESEPARATOR
- public static short SPACESEPARATOR
- public static short MENUITEM
- public static short RESPONSIBILITYITEM
- public static short LOVRUNTIMEITEM
- public static short MULTILISTRUNTIMEITEM
- public static short DESCFLEX
- public static short KEYFLEX
- public static short SEGMENTLOV
- public static short SEGMENTTEXT
oracle.apps.mwa.beans.FlexFieldBeanpublic class FlexfieldBean extends MWABean implements oracle.apps.fnd.flexj.event.FlexfieldListener- It represents the flexfield in the Mobile Applications
- Constructor -
public FlexfieldBean(oracle.apps.fnd.flexj.Flexfield flexfield, oracle.apps.mwa.container.Session session) - Maintains boolean variables and getters and setters for readonly, hidden and required (
private boolean m_readonly, m_hidden, m_required): public boolean isRequired()public void setRequired(boolean requiredFlag)public void setHidden(boolean hiddenFlag)public void setReadonly(boolean readOnlyFlag)public boolean isReadonly()- Important Flexfield related APIs:
public Flexfield getFlexfield()
protected boolean addSegmentBean(Segment Seg)
protected void removeSegmentBean(Segment Seg)
Following are three most frequently used beans on Mobile Application Pages:
oracle.apps.mwa.beans.TextFieldBeanpublic class TextFieldBean extends InputableFieldBean
- Constructor:
public TextFieldBean() - Frequently used properties and their getters and setters inherited from FieldBean:
- name, prompt, hidden
- Frequently used properties and their getters and setters inherited from InputableFieldBean:
- editable (
protected boolean m_editable) - required (protected boolean m_required)
- display length (protected int m_length)
- value (protected java.lang.String m_value)
- value type (
protected java.lang.String m_valueType) - Possible values are: S - String, N - Number, D - Date, C - Calculation, R - Range
- Maintains password property (
protected boolean m_password) public boolean isPassword()
public void setIsPassword(boolean IsPassword)
- Maintains navigation to next page property (
protected java.lang.String m_nextPageName) public java.lang.String getNextPageName()
public void setNextPageName(java.lang.String NextPageName)
oracle.apps.mwa.beans.LOVFieldBeanpublic class LOVFieldBean extends InputableFieldBean- Constructor: public LOVFieldBean()
- Frequently used properties and their getters and setters inherited from FieldBean:
- name, prompt, hidden
- Frequently used properties and their getters and setters inherited from InputableFieldBean:
- editable, required, display length (length), value, value type
- Maintains navigation to next page property (
protected java.lang.String m_nextPageName) public java.lang.String getNextPageName()
public void setNextPageName(java.lang.String NextPageName)
- Maintains LOV Statement (protected java.lang.String m_lovStatement)
- This is mandatory to be set.
- Store SQL query or PL/SQL procedure with a reference cursor output parameter.
public void setlovStatement(java.lang.String LovStatement)
public java.lang.String getlovStatement()
- Maintains key names, prompt, types, rendered property of the subfields of the Lov page, (
protected java.lang.String[] m_subfieldNames, protected java.lang.String[] m_subfieldPrompts, protected java.lang.String[] m_subfieldTypes, protected boolean[] m_subfieldDisplays). - The size of these arrays should be same.
public java.lang.String[] getSubfieldNames()
public void setSubfieldNames(java.lang.String[] SubfieldNames)
public java.lang.String[] getSubfieldPrompts()
public void setSubfieldPrompts(java.lang.String[] SubfieldPrompts)
public java.lang.String[] getSubfieldTypes()
public void setSubfieldTypes(java.lang.String[] SubfieldTypes)
public boolean[] getSubfieldDisplays()
public void setSubfieldDisplays(boolean[] SubfieldDisplays)
- Maintains key names of the input parameters and parameter types (
protected java.lang.String[] m_inputParameters, protected java.lang.String[] m_inputParameterTypes) public java.lang.String[] getInputParameterTypes()
public void setInputParameterTypes(java.lang.String[] InputParameterTypes)
public java.lang.String[] getInputParameters()
public void setInputParameters(java.lang.String[] InputParameters)
- Maintains values returned from LOV or selectec values (
protected java.util.Vector m_selectedValues) public java.util.Vector getSelectedValues()
public boolean isPopulated()
- Maintains lov validation required property (
protected boolean m_validateFromLOV) - Specifies if user has to always go through LOV page - if false,
value in the field is accepted without validation. Default is True. public void setValidateFromLOV(boolean validateFromLOV)
public boolean isValidateFromLOV()
oracle.apps.mwa.beans.ButtonFieldBeanpublic classextends FieldBeanButtonFieldBean
- Constructor: public
ButtonFieldBean
() - Frequently used properties and their getters and setters inherited from FieldBean:
- name, hidden (behavior of prompt is different for buttons as it includes accelerator keys)
- Maintains button prompt property with accelerator key (protected java.lang.String m_prompt):
public void setPrompt(java.lang.String s)
public void setPrompt(java.lang.String s)
- If we call setPrompt("&Done"), getPrompt() will return "Done".
- 'D' will be the hot key for "Done" button
- Maintains navigation to next page property (
protected java.lang.String m_nextPageName) public java.lang.String getNextPageName()
public void setNextPageName(java.lang.String NextPageName)
- Maintains accelerator key enable/disable property (
protected boolean m_enableAcceleratorKey) public void setEnableAcceleratorKey(boolean b)
public boolean isAcceleratorKeyEnabled()
Please proceed to MSCA/MWA Framework - Custom Development and Extension - Part 2 to read more.
Previous Read: Oracle MSCA/MWA Framework - Introduction
Previous Read: Oracle MSCA/MWA Framework - Introduction